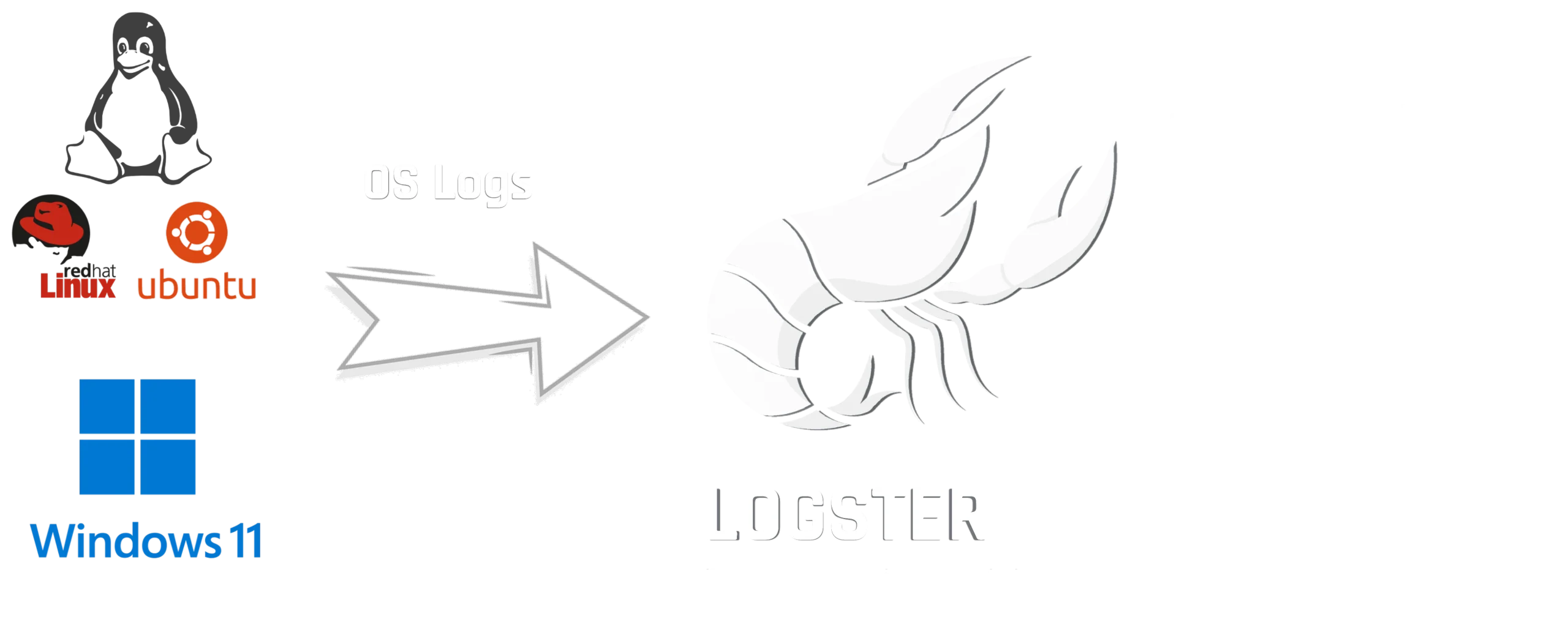
Logster Cybersecurity Model continuously digests security logs from Windows and Linux
operating systems to seamlessly detect MITRE ATT&CK TTPs and zero-day cyber threats in
real time.





We are a forward-thinking digital company focused on delivering intelligent AI-driven solutions. From data analytics to machine learning systems, we help businesses optimize operations, reduce costs, and make smarter decisions.
By combining technical expertise with real-world problem solving, we create scalable AI solutions that drive measurable impact and long-term growth across industries.
Eliminate detection lag with direct telemetry streaming. Logster.ai ingests native OS events from endpoints to our inference engine in real-time, providing sub-second visibility into emerging threats without the baggage of heavy agents.
Accelerate incident response with MITRE-mapped intelligence. Logster.ai enriches raw telemetry into high-confidence alerts with full process lineages and attack timelines, reducing alert fatigue by prioritizing high-risk sequences over isolated system events.
Achieve full-stack visibility across hybrid environments. Logster.ai integrates directly with Windows Sysmon and PowerShell for script-level analysis, while leveraging Linux auditd and eBPF telemetry to capture kernel-level system calls with minimal performance impact.
Streamline forensics with multi-stage attack reconstruction. Logster.ai delivers enriched alerts mapped to the MITRE ATT&CK framework, providing automated event correlation and visual timelines that allow analysts to trace the full kill chain from initial access to data exfiltration.
Transmit encrypted telemetry to our real-time inference pipeline or on-prem engine. Our high-velocity streaming architecture processes logs with sub-second latency, ensuring your detection capabilities keep pace with active, evolving threats.
Securely transmit telemetry to our real-time inference pipeline via encrypted streams. Whether cloud-hosted or on-prem, our engine processes high-velocity logs with sub-second latency to ensure detection keeps pace with active attacks.
Apply multi-dimensional analysis to correlate telemetry across time, users, and hosts. Our AI engine identifies sophisticated attack patterns by distinguishing malicious deviations from legitimate administrative activity in real time.
Deliver high-fidelity, MITRE-mapped notifications to your SOC. Logster.ai prioritizes critical attack sequences over isolated events, providing the enriched context and automated timelines required for rapid incident response.
Quick answers to common questions about our AI services & solutions
Logster.ai supports multiple Windows and Linux operating system logs. Logster utilizes Windows
Security Audit Logs, PowerShell Operational Logs, and Sysmon artifacts to provide full telemetry coverage
for real-time threat detection.
Our hybrid AI models combine behavioral baselining, statistical anomaly detection, and machine learning to identify deviations and suspicious activity in real time — even for unknown or fileless attacks.
Yes. logster.ai supports fully on-prem inference nodes for organizations with strict data residency or compliance requirements.
All data is encrypted in transit using TLS. You can also deploy fully on-prem for zero cloud exposure. Optional zero-log mode is available to meet privacy requirements.
Yes. By learning normal host and process behavior, our AI can detect suspicious patterns and deviations even without signatures.
Our system uses per-host baselining, adaptive thresholds.
Alerts are typically delivered within seconds of detection, enabling real-time response to incidents.
Yes, enterprise plans include dedicated support.
Only if using cloud-hosted inference. On-prem deployments can run entirely offline.
Fileless malware, suspicious PowerShell scripts, privilege escalation attempts, lateral movement, unusual kernel activity, and other behavior-based anomalies.
Our team is here to help with questions about logster.ai, deployments, and detection capabilities.